How to erase FEELMYFASHION.COM virus (Removal Guide)
How to get rid of EMPERMIN.COM virus (Removal Guide)
How to clear away ELTOLLBRU.COM virus (Removal Guide)
How to remove COPYBIDASP.LIVE virus (Removal Guide)
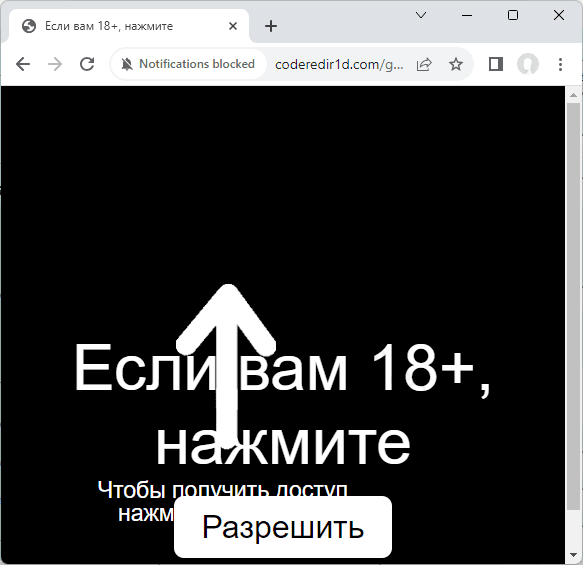
How to remove CODEREDIR1D.COM virus (Removal Guide)
How to get rid of ATERASELCOGRIA.CO.IN virus (Removal Guide)
How to remove ARTNEWTABS.COM virus (Removal Guide)
How to delete ABSCONDSLAB.COM virus (Removal Guide)
How to erase 1WYDBG.TOP virus (Removal Guide)
How to delete TINYFY.CC virus (Removal Guide)
How to eliminate NOWCAPTCHAHERE.EW.R.APPSPOT.COM virus (Removal Guide)
How to get rid of NEWS-MINUWI.CC virus (Removal Guide)
How to get rid of DISCOVERRESULTSFAST.COM virus (Removal Guide)
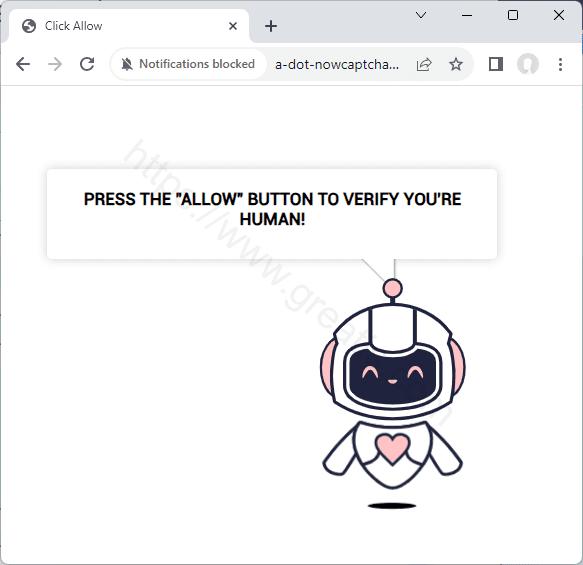
How to cut off A-DOT-NOWCAPTCHAHERE.EW.R.APPSPOT.COM virus (Removal Guide)

Between July and September, DarkGate malware attacks leveraged compromised Skype accounts to infect targets via messages with VBA loader script [...]
How to get rid of SYSTEM-NOTIFY.APP virus (Removal Guide)
How to get rid of SYSCOD.XYZ virus (Removal Guide)
How to remove PROMSMOTION.COM virus (Removal Guide)
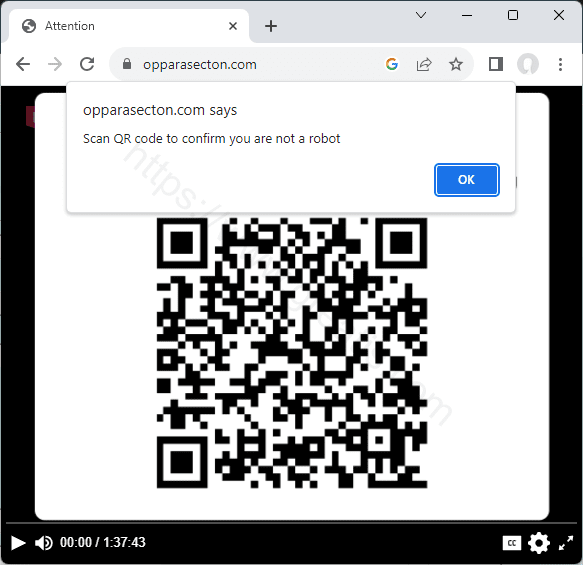
How to erase OPPARASECTON.COM virus (Removal Guide)
How to clear away OPPARASECTION.COM virus (Removal Guide)
How to remove NINDSSTUDIO.COM virus (Removal Guide)
How to clear away NEWS-XOWADA.CC virus (Removal Guide)
How to clear away NEWS-NOGOXE.CC virus (Removal Guide)
How to clear away NEWS-LAZOZE.CC virus (Removal Guide)
How to delete NEWS-FULIFU.COM virus (Removal Guide)
How to uninstall NEWS-FEJEGA.CC virus (Removal Guide)
How to delete ISRAELDATE.XYZ virus (Removal Guide)
How to uninstall GETSEARCHINGREDIRECT.COM virus (Removal Guide)
How to clear away FONDSBOX.COM virus (Removal Guide)
How to delete ELITEDATINGEXPERIENCE.TOP virus (Removal Guide)
How to delete COINS.EPE-OLAUD.TOP virus (Removal Guide)
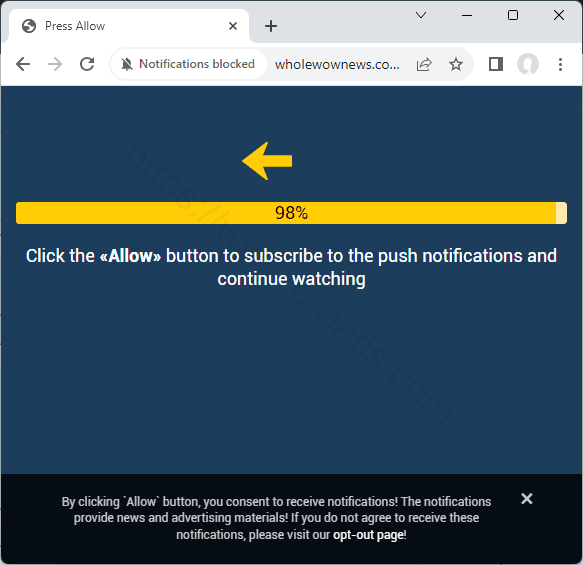
How to cut off WHOLEWOWNEWS.COM virus (Removal Guide)
How to eliminate OUMSOPAZ.TOP virus (Removal Guide)
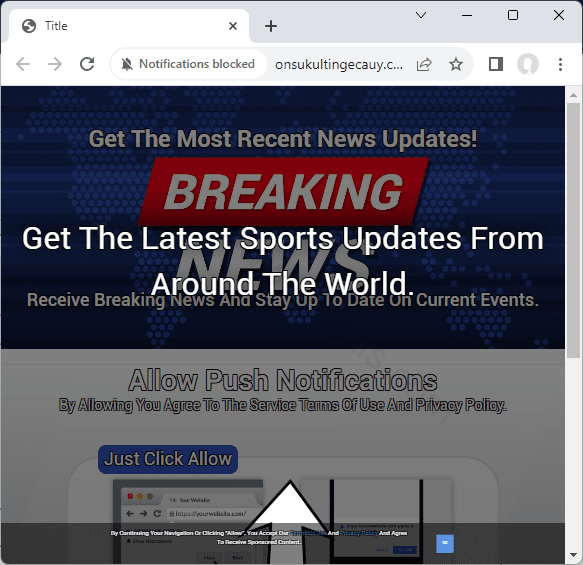
How to erase ONSUKULTINGECAUY.COM virus (Removal Guide)
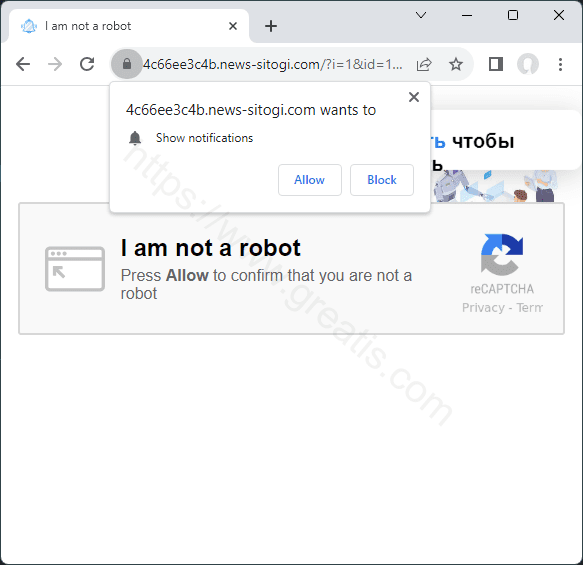
How to delete NEWS-SITOGI.COM virus (Removal Guide)
How to cut off NEWS-FUKIHE.CC virus (Removal Guide)
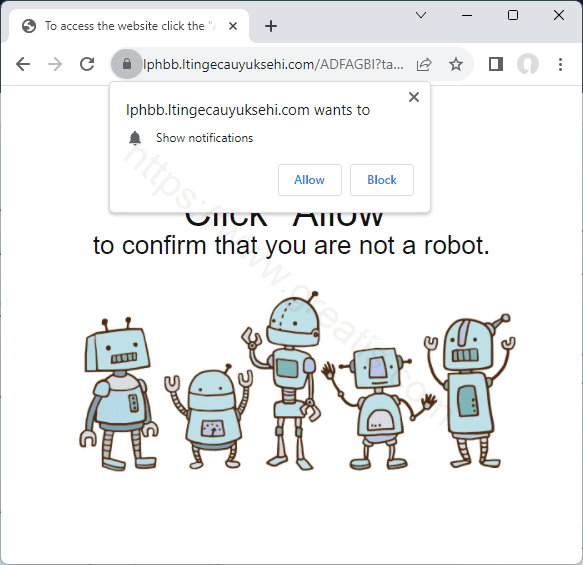
How to eliminate LTINGECAUYUKSEHI.COM virus (Removal Guide)
How to remove EURONEWS.WIKI virus (Removal Guide)
How to cut off DEEPCOREMINER.TOP virus (Removal Guide)
How to cut off CCUEFOOTTRIP.LIVE virus (Removal Guide)