Noskrnl rootkit is spread by e-mail. Often attachment has the file name: "SuperLaugh.exe" or the similar name.
RegRun detects the working driver (not hidden) during the "Scan for Viruses" process:
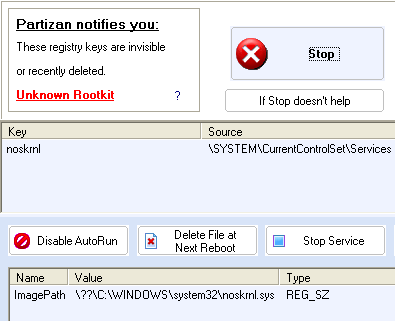
Also it detects the open process immediately after reboot:
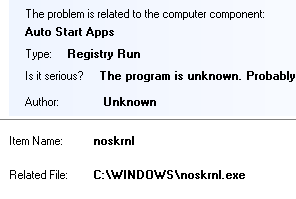
But the noskrnl.exe file is hidden by rootkit technology.
Noskrnl uses "noskrnl" subkeys in the HKLM\System\CurrentControlSet\Services and under all other "ControlSet" keys.
"Noskrnl.exe" starts from registry Run key. Driver is used for hiding the rootkit files.
Noskrnl.exe is used for propagation.
Noskrnl.config is located in the Windows folder. It sets the used port and some other settings.

In addition, we need to remove "Noskrnl.config" from the Windows folder.

|
Good luck!
Dmitry Sokolov |