It is not invisible rootkit. It is a mail worm used rookit technology.
Usually you can receive it by e-mail sent from infected computer. Feebs attaches zipped "hta" file to each sent e-mail message.
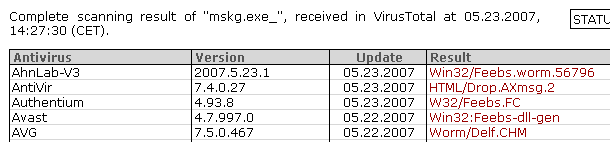
Unfortunately most of antiviral software could not detect it and the users who trust their antiviral software are infected.
Other files are stored in the Windows\System32 folder.
The DLL file has random name with mask "ms??32.dll" (where ? is any character). The executable file looks like "ms??.exe".
Executable file is used to reproduce infection and for loading its DLL into memory.
The DLL is a user mode rootkit and it hides the rootkit′s Active Setup subkey.
In additional, Feebs tries to deactivate several antiviral software. Feebs is not rock but unfortunately most of antiviral software doesn′t detect it. Getting the latest virus database is required.
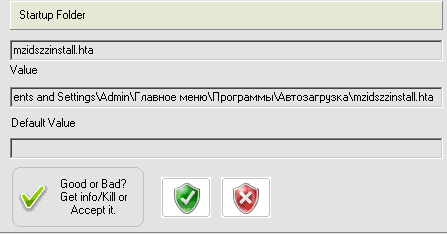
RegRun prevents "hta" file from executing and it is able to prevent adding Feebs to auto startup.
Choose "Scan for Viruses".
Reanimator will detect the "c:\windows\csrss.exe" file.
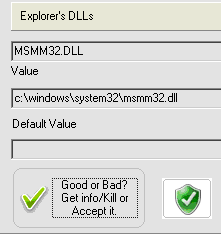
Click on the "Good or Bad" and choose "It′s useless for me. Kill it!" in the next screen.
After that Reanimator will catch the DLL file.
Click on the "Reboot" button to apply changes and continue scanning after reboot.
The scanning process will continue after you log on to the Windows...
Reanimator will detect the "EXE" file.
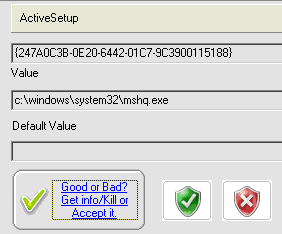
Kill it and you can choose exit Reanimator without reboot to continue Windows boot process.
Virus has been deleted successfully!

|
Good luck!
Dmitry Sokolov |