Greatis Software support expert detected suspicious file in the user′s system report file. This file is generated by free Greatis Software Reanimator software.
It was the "c:\windows\system32\ntsystem.exe". This file was registered in the "Run" startup keys as "gwiz".
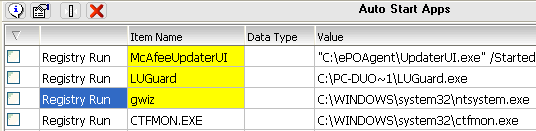
But deletion of the "ntsystem.exe" file doesn′t not provide us any success. The file is automatically recreated after reboot. Catty tried to delete "ntsystem.exe" at Windows restart using the newest Greatis Software product called "Partizan". Partizan doesn′t use Windows "PendingFileRename key for deleting. It uses own Native API application and Partizan successfully deleted "ntsystem.exe".

But after successful Windows loading we got "ntsystem.exe" again.
Catty asked a user for getting "xpbootlog.txt" report made by Greatis Software Bootlog XP tool. We analyzed received "xpbootlog.txt" and found the strange file: NTOSKRNL.DLL.

It looks like the Windows related system file. NTOSKRNL.EXE is a good known Windows system file. But NTOSKRNL.DLL is not the same.
After that we opened xpbootlog.txt using Bootlog XP software.
We found that the DLL was loaded by Winlogon. NTOSKRNL.DLL is registered as Winlogon Notification DLL.
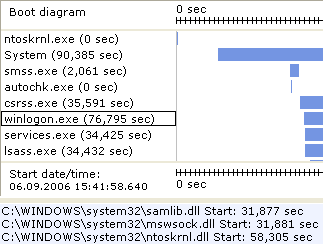
NTOSKRNL.DLL is a user mode rootkit. It hides its presence in the registry and in the loaded modules listing.
You could not delete it using standard Windows deletion methods.
You will see the "RegRun Partizan" on the Windows blue boot screen in the same moment when Windows checking hard drives.
Look at the messages on the screen to be sure that the dangerous files are deleted.

|
Good luck!
Dmitry Sokolov |
Jack Nelson