How to get rid of NHQKD.CLICK virus (Removal Guide)
How to get rid of MANG0BANANASHAK3.XYZ virus (Removal Guide)
How to get rid of KSLIY.DEVELOPEDSEVE.COM virus (Removal Guide)
How to get rid of HULQOEB.CLICK virus (Removal Guide)
How to erase GOODSERCHEZ.COM virus (Removal Guide)
How to delete FYALLUSAD.TOP virus (Removal Guide)
How to get rid of DUALSALE4.XYZ virus (Removal Guide)
How to remove DOGUHTAM.XYZ virus (Removal Guide)
How to remove DEVELOPEDSEVE.COM virus (Removal Guide)
How to eliminate DE-MI-NIS-NER2.INFO virus (Removal Guide)
How to clear away CHECK-TL-VER-198-E.BUZZ virus (Removal Guide)
How to get rid of 1WSBLW.LIFE virus (Removal Guide)
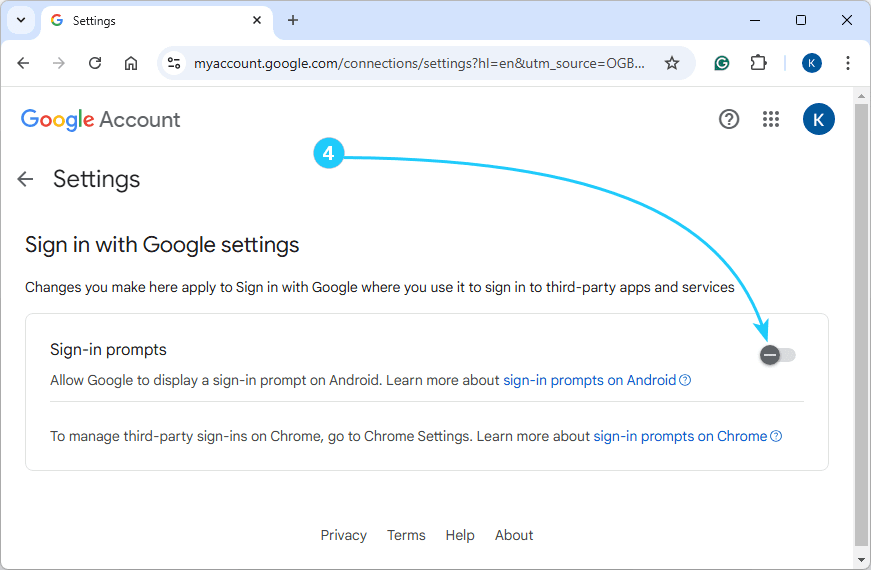
If you use a browser signed in to your Google account, you may have noticed pop-ups on many websites asking [...]

The phishing-as-a-service (PhaaS) platform "FlowerStorm" has gained traction after the Rockstar2FA service suffered a partial collapse in November 2024. Rockstar2FA [...]
How to eliminate VFIREWALL.CO.IN virus (Removal Guide)
How to delete RPRLDPNWS2.XYZ virus (Removal Guide)
How to uninstall POOLIUQ.CLICK virus (Removal Guide)
How to delete NEWS-BKUDOTI.XYZ virus (Removal Guide)
How to delete NEWS-BKEPERU.XYZ virus (Removal Guide)
How to uninstall NEWEQI.CLICK virus (Removal Guide)
How to uninstall NETWORKFLO.CO.IN virus (Removal Guide)
How to get rid of LAR3VOLUT1ON15H3R3.TOP virus (Removal Guide)
How to uninstall HEYBEYQ.CLICK virus (Removal Guide)
How to eliminate EESSEHORDS.CO.IN virus (Removal Guide)
How to get rid of BFREJQ.CLICK virus (Removal Guide)
How to get rid of BFERQR.CLICK virus (Removal Guide)
How to cut off BETQUESTIONS4.XYZ virus (Removal Guide)
How to get rid of ARTICLESSEA5.XYZ virus (Removal Guide)
How to uninstall 0.MAJORLINKER.COM virus (Removal Guide)
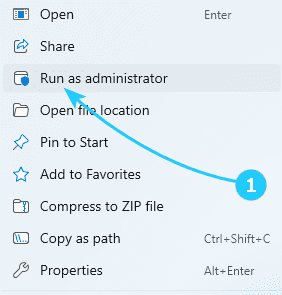
If you encountered the error The requested operation requires elevation with error code 740 (or 0x000002E4), and you were unable [...]
How to get rid of NEWS-BPIBORO.XYZ virus (Removal Guide)
How to get rid of NEWS-BNIGEBI.XYZ virus (Removal Guide)
How to get rid of NEWS-BLURABI.XYZ virus (Removal Guide)
How to get rid of N1C3TR33.TOP virus (Removal Guide)
How to get rid of GOBOKSEHEE.NET virus (Removal Guide)
How to get rid of FORBESTBETS.COM virus (Removal Guide)
How to get rid of 1XLITE-581089.TOP virus (Removal Guide)
User Account Control (UAC) is a means of protecting against potentially dangerous actions and running software that can harm your [...]
How to get rid of TOPTVTADINC.AZUREWEBSITES.NET virus (Removal Guide)
How to delete TOPCUTELLGROUP.AZUREWEBSITES.NET virus (Removal Guide)