How to uninstall TRAFFIC.DEALSFOR.LIFE virus (Removal Guide)
How to eliminate RECUTASSEUCCARS.COM virus (Removal Guide)
How to clear away PSADSAURSURVEY.TOP virus (Removal Guide)
How to get rid of MAGNLFICENTDATE.NET virus (Removal Guide)
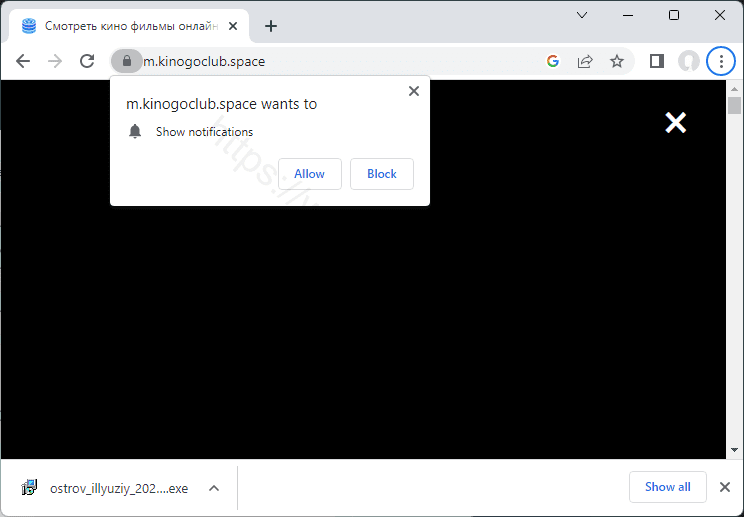
How to uninstall M.KINOGOCLUB.SPACE virus (Removal Guide)
How to remove LURDOOCU.COM virus (Removal Guide)
How to erase LILUSTRLOUSDATE.COM virus (Removal Guide)
How to uninstall JOATHATH.COM virus (Removal Guide)
How to uninstall GO.GOASERV.COM virus (Removal Guide)
How to get rid of GAMING-TRENDING-NEWS.COM virus (Removal Guide)
How to erase DATEMEUP.TOP virus (Removal Guide)
How to delete COREAREERA.LIVE virus (Removal Guide)
How to clear away BYBYGNOM.COM virus (Removal Guide)
How to uninstall BATTLEHAMMER.TOP virus (Removal Guide)
How to erase 0.DM16.BIZ virus (Removal Guide)
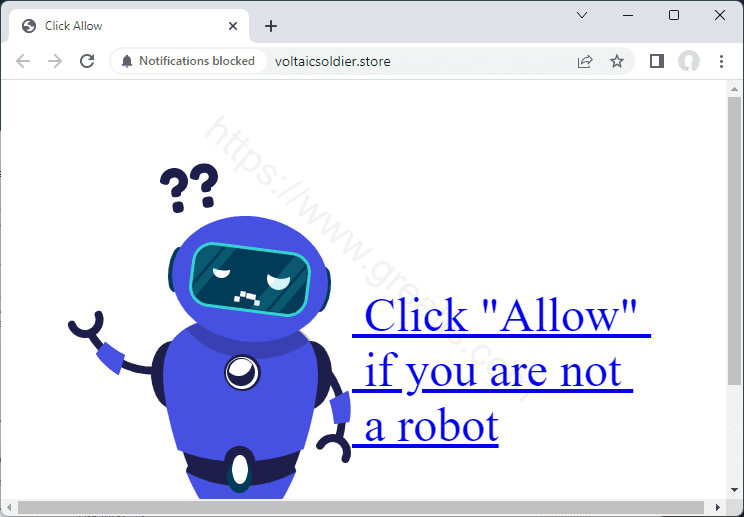
How to delete VOLTAICSOLDIER.STORE virus (Removal Guide)
How to get rid of UP4W3.ONLINE virus (Removal Guide)
How to eliminate SOALIZED.COM virus (Removal Guide)
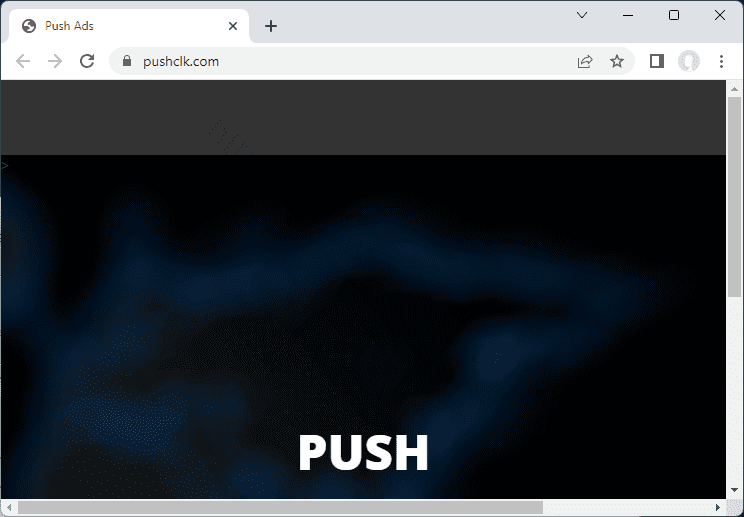
How to delete PUSHCLK.COM virus (Removal Guide)
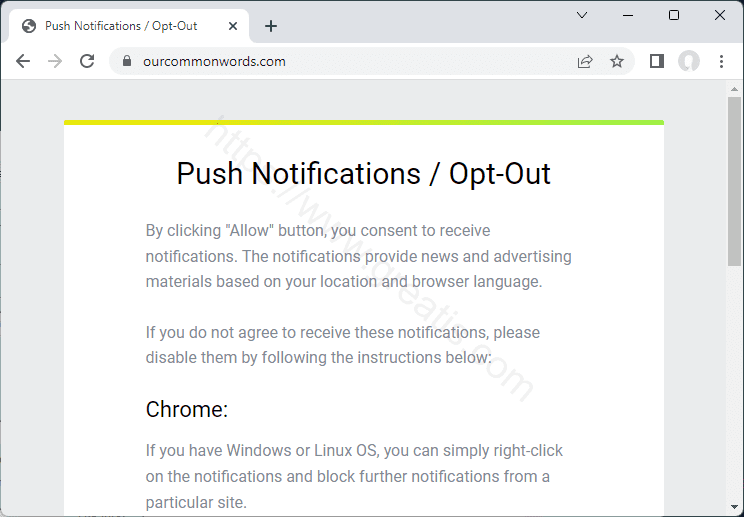
How to erase OURCOMMONWORDS.COM virus (Removal Guide)
How to cut off MENTRANDINGSWON.COM virus (Removal Guide)
How to cut off MAMMA.COM virus (Removal Guide)
How to get rid of GOSTEADYCOMRADE.STORE virus (Removal Guide)
How to uninstall GL0W-4RTIS4N.XYZ virus (Removal Guide)
How to eliminate GETLUCKYPRIZE.TOP virus (Removal Guide)
How to remove GETLUCKYPRIZE.COM virus (Removal Guide)
How to cut off GALOTOP1.COM virus (Removal Guide)
How to uninstall ESAIPROS.COM virus (Removal Guide)
How to erase DOMAINANALYTICSAPI.COM virus (Removal Guide)
How to cut off AWNORLAG.LIVE virus (Removal Guide)
How to clear away ACTOUNTOLOUTE.COM virus (Removal Guide)

QBot malware has been spotted to abuse a DLL hijacking vulnerability in the Windows 10 WordPad to infect targeted devices. [...]
How to cut off XML-V4.TRAFFICMOOSE.COM virus (Removal Guide)
How to eliminate WWW.EFUN.TOP virus (Removal Guide)
How to delete SHUGNAIS.NET virus (Removal Guide)
How to get rid of OPSOOMET.NET virus (Removal Guide)
How to erase GUSSELLSZ.COM virus (Removal Guide)
How to cut off CHROME-ERROR.ONLINE virus (Removal Guide)
How to get rid of BIFIPUAD.COM virus (Removal Guide)
How to cut off 7JHAWD7.COM virus (Removal Guide)